Time for Binance to Step Away from Twitter
Elon Musk's Twitter Revamp: A Potential Game-Changer for DOGE and Cryptocurrencies in General
2020 Twitter Hacker Receives 5-Year Sentence for Cryptocurrency Theft and SIM Swapping Scheme
The most evil cryptocurrency and nonfungible token (NFT) schemes that are now active on Twitter have been selected by cybersecurity specialist Serpent.
The analyst is the creator of Sentinel, an artificial intelligence and community-powered crypto threat mitigation solution, and has 253,400 followers on Twitter.

Serpent described how scammers target naive cryptocurrency users by using imitation websites, URLs, accounts, hacked verified accounts, bogus projects, false airdrops, and lots of malware in a 19-part thread published on August 21.
In light of the current uptick in protocol attacks and crypto phishing schemes, one of the more concerning tactics has emerged. According to Serpent, the Crypto Recovery Scam is employed by criminals to defraud those who just lost money due to a widespread hack, saying:
“Simply put, they attempt to target people who have already been scammed, and claim they can recover the funds.”
These con artists, according to Serpent, pose as blockchain developers and look for individuals who have recently been the target of a significant hack or exploit. They then persuade them to pay a fee to create a smart contract that can help them retrieve their stolen cash. They "take the fee and run" instead.
This was demonstrated when the community was warned by Heidi Chakos, the host of the YouTube channel Crypto Tips, to be wary of con artists proposing a fix for the vulnerability, following the multimillion-dollar exploit affecting Solana wallets earlier this month.
Another tactic makes use of current weaknesses. The analyst claims that the Fake Revoke.Cash Scam uses a "state of urgency" to persuade consumers to click a malicious link by informing them that their cryptocurrency assets may be at jeopardy.
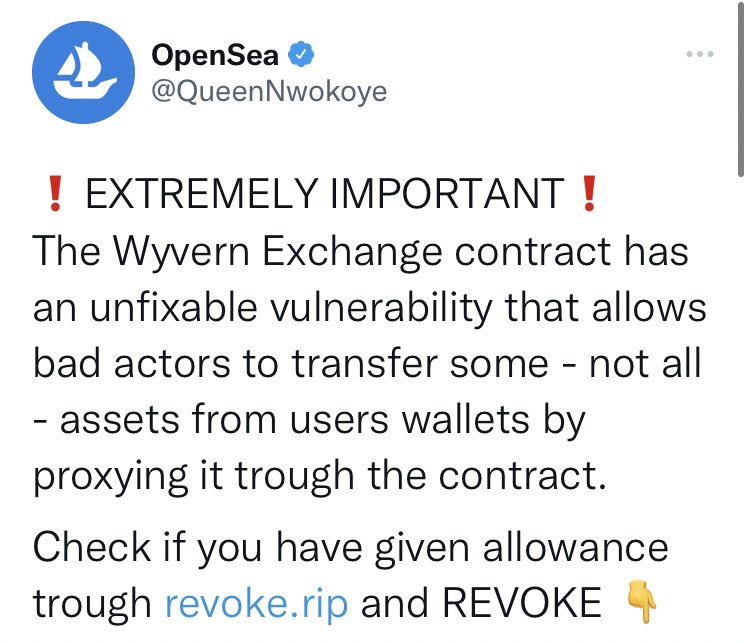
Another method involves changing one of the letters in a phishing URL with a Unicode lookalike in order to make it appear almost identical to a legitimate one. Another tactic involves con artists hacking a verified Twitter account, renaming it, and using it to promote bogus airdrops or mints while posing as a person of authority.
The remaining frauds go after people who wish to participate in a get-rich-quick scheme. This includes the Uniswap Front Running Scam, which is frequently represented by spam bot messages instructing users to view a video on how to "earn $1400/DAY front-running Uniswap" but really connives to get them to send their money to the wallet of a con artist.
A Honeypot Account is another tactic, where consumers are allegedly given a private key to unlock a loaded wallet. However, when customers try to contribute cryptocurrency to pay for the transfer of coins, a bot promptly sends them to the wallets of the con artists.
Other strategies include hiring phony artwork from NFT artists or asking valuable NFT collectors to "beta test" a new play-to-earn (P2E) game or project. The trick, however, is simply a pretext to send users malicious files that can collect browser cookies, passwords, and extension data in both instances.
According to a Chainalysis analysis released last week, the market exodus of novice cryptocurrency users and declining asset prices have caused a 65% decline in 2022's revenue from crypto frauds. Year-to-date revenue from cryptocurrency scams is already $1.6 billion, down from roughly $4.6 billion in the previous year.















