Cryptographic Functions
Cryptographic Functions latest news, images, analysis about A cryptographic hash function (CHF) is a hash algorithm (a map of an arbitrary binary string to a binary string with a fixed size of $${\displaystyle n}$$ bits) that has special properties desirable for a cryptographic application: the probability of a particular $${\displaystyle n}$$-bit output result (hash … See more
Most Popular News for Cryptographic Functions
Cryptographic hash function - Wikipedia
Cryptography - Wikipedia
Cryptography Functions - Win32 apps | Microsoft Learn
Cryptographic Hash Functions and Birthday Paradox
21:19 - 2 years ago
Cryptographic Hash Functions and Birthday Paradox.
We've given you our best advice, but before you read Cryptographic Functions, be sure to do your own research. The following are some potential topics of inquiry:
What is Cryptographic Functions?
What is the future of Cryptographic Functions?
How to Cryptographic Functions?
Our websites are regularly updated to ensure the information provided is as up-to-date as possible in regards to Cryptographic Functions. Take advantage of internet resources to find out more about us.
Cryptographic Hash Functions: Definition and Examples
What Is a Cryptographic Hash Function? - Lifewire
Cryptographic Hash Functions Explained: A Beginner’s …
Lecture 21: Cryptography: Hash Functions - MIT …
What is cryptography? | IBM
Cryptographic function - Glossary | CSRC
Cryptographic hash function - MDN Web Docs
What is cryptography? How algorithms keep …
Hashes and Message Digests - Department of Computer Science
What is Cryptography? Definition, Importance, Types | Fortinet
Understanding Cryptography’s Meaning and Function - Linode
Cryptography Hash functions - Online Tutorials Library
What Are Cryptographic Hash Functions? | Synopsys Blog
Hash Functions and list/types of Hash functions - GeeksforGeeks
Cryptography and its Types - GeeksforGeeks
Understanding Cryptographic Hash Functions: A Guide
Cryptographic Functions (Transact-SQL) - SQL Server | Microsoft …
Videos of Cryptographic Functions
Exploring Cryptographic Hash Functions
1:08 - 2 years ago
checkout new video "The Backbone of Digital Security: Exploring Cryptographic Hash Functions"
Introduction to Cryptography: Security of RSA
7:38 - 2 years ago
Learn about prime factor and public-key selection as well as benefits and pitfalls of RSA cryptography. While RSA is more ...
Hash Functions from Block Ciphers, Merkle-Damgard, and Sponge Functions
10:48 - 2 years ago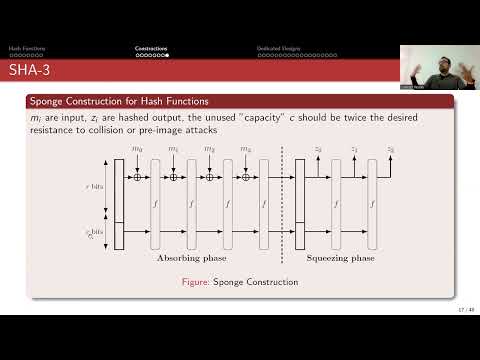
#cipher #cybersecurity #cihangirtezcan #crypto Hash Functions from Block Ciphers, Merkle-Damgard, and Sponge Functions.
What are the core concepts in Cryptography and Security?
0:13 - 2 years ago
Dive into the fascinating world of Cryptography and Security with our latest YouTube Short! This video is designed for anyone ...