
The security consultant, who previously blew the whistle on unethical practices, asserts that the internet's underlying infrastructure is ill-equipped to protect individuals' privacy.

The security consultant, who previously blew the whistle on unethical practices, asserts that the internet's underlying infrastructure is ill-equipped to protect individuals' privacy.

On October 2, the Singapore Grand Prix is held.

Only the programs that run on a blockchain can guarantee its security.

Module 3 – Cryptographic Solutions In this module, we will explore what makes encryption work. We will look at what types of ...
We've given you our best advice, but before you read Cryptography Solution Manual, be sure to do your own research. The following are some potential topics of inquiry:
What is Cryptography Solution Manual?
What is the future of Cryptography Solution Manual?
How to Cryptography Solution Manual?
Our websites are regularly updated to ensure the information provided is as up-to-date as possible in regards to Cryptography Solution Manual. Take advantage of internet resources to find out more about us.

Stateful hash-based signatures provide thorough security and a high level of maturity. However, their requirement of proper ...
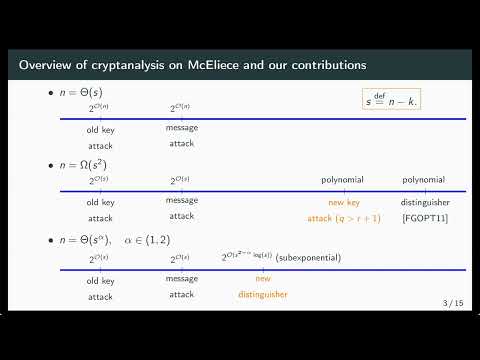
Cryptanalysis of Post-Quantum Cryptography is a session presented at Asiacrypt 2023, chaired by Thomas Espitau.

Reflecting on a disastrous Xbox experience, I was reminded of so many frustrating interactions I've had with various software and ...

Now that the quantum era is upon us, the question arises: How do you ensure your organisation is “quantum-ready”? With some ...